Data Security
With the new laws in terms of Data Privacy and Data Protection, compliances with international standards have an important factor in choosing a Cloud Provider, especially when dealing with Backup.
It's easy to figure out how important is to us to guarantee the security of data to our clients, given the fact that an hypothetical negligence in the supply of 1Backup would determine a compromised position on the market as Providers.
We suggest to take some time to study the compliance of your provider -if you are already using some cloud services- and to evaluate carefully the offers you can find on the Web.
This document describes the security levels guaranteed by 1Backup with the aim of providing answers on such topic to the client.
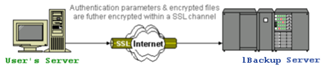
128-BIT SECURE SSL COMMUNICATION
All the communication between the 1Backup Server and the server/pc of the client happens on an 128-bit SSL connection (SSL stands for Secure Socket Layer). Even in case of backup files being spoofed while on the Internet, the attacker could not decipher the content.
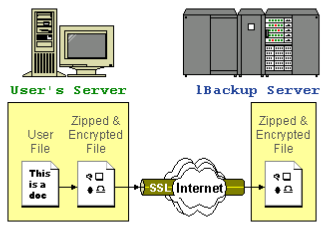
SAVED DATA ARE CIPHERED IN A SECURE WAY
All the files are first compressed and then ciphered according to the algorithm choose by the client before being uploaded to the 1Backup Server. Data, when stored on the 1Backup Server, is like a pile of files with random content and no way identifiable.
DECRYPTION KEY MUST BE CAREFULLY GUARDED
The encryption key used to cipher your files is stored only on the server/computer on which the backup job is created, and only you know it! Therefore, only who has the decryption key can see the content of data stored on the 1Backup Server. However, that also means if the key gets unfortunately lost, there is no way to restore data.
Technical details:
The cryptographic key for each backup set is stored in the config.sys file which is located in different paths depending on the OS used.
If the client software (ie. the Agent) can't find the config.sys file, the request of inserting the decryption password is asked at the next execution of a backup or restore job, thus creating a new config.sys in the system.
The best ciphering algorithm
The algorithm used to cipher your files is Advanced Encryption Standard (AES) operating at 256-bit. AES is the first cipher algorithm available to the public and approved by the National Security Agency (NSA) to safeguard top secret information.
Decrypting a 256-bit ciphered file takes 1,46 x 1054 years
A 256-bit key has circa 2256 (or 1,16 x 1077) possible combinations. If you had a super computer like the Tianhe-1A with 14.336 Xeon X5670 (6 Core, da 2,93 Ghz) processors, developed by the Chinese National University of Defense Technology in October 2010, you would have to wait 1,46 x 1054 years before trying all the possible combinations. Still, you would have to test all the combinations found.
A brute force attack on this algorithm to try all the possible combinations would take:
1,16 x 1077
---------------- seconds ~ 4,621 x 1061 sec
2,507 x 1015
Which corresponds to ~ 1,46 x 1054 years
Considering all those factors, you can be assured that your data is 100% safe.